
by Stephen Kennen | Dec 17, 2024 | Business Continuity, Network Security, Tech Tips
How careful are you with online security? You probably know the basics – avoid phishing emails, skip sketchy downloads, and don’t click suspicious links. But there’s a new player in the malware game, and it doesn’t just steal your details – it frustrates...

by Stephen Kennen | Dec 1, 2024 | Business Continuity, Network Security
Spyware is more than just a buzzword – it’s a serious and growing cybersecurity threat. Even tech giants like Google are sounding the alarm, warning about the “real-world harm” it can cause. But what is spyware exactly, and how can you protect your business from...

by Stephen Kennen | Jul 24, 2024 | Business Continuity, Network Security
On Friday July 19, 2024, a routine software update from CrowdStrike, a leading cyber security company, caused a major issue affecting an estimated 8.5 million Windows computers. Proactive IT does not use CrowdStrike software, so our customer networks were not...
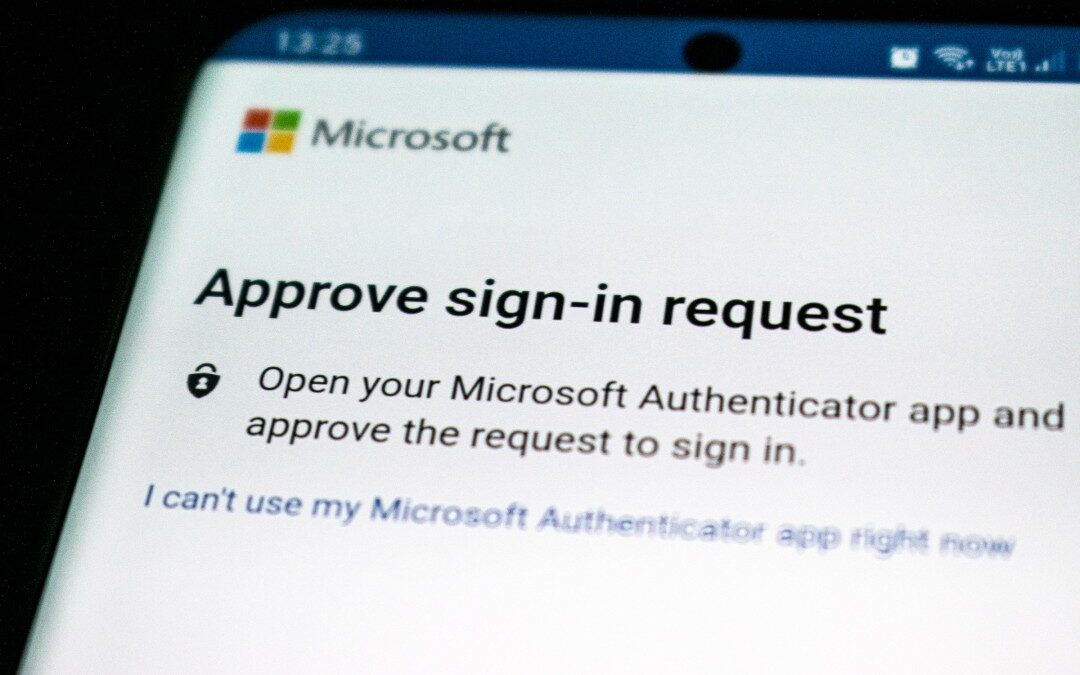
by Stephen Kennen | May 7, 2024 | Network Security
As described in a previous blog post, we have observed a concerning increase in successful phishing attacks against Microsoft 365 accounts that have MFA enabled and enforced. We have invested heavily in researching available options that will mitigate the risks posed...

by Stephen Kennen | Feb 22, 2024 | Network Security
We’ve observed a concerning rise in successful phishing attacks leading to compromised email accounts. Quite simply, the bad guys are getting more and more sophisticated. To protect your organization, it is important that you remain informed and vigilant. Here’s...

by Stephen Kennen | Jan 23, 2024 | Network Security
Last week, one of our clients experienced an interesting phishing scam. Our client was not the “target” – in fact, the scam targeted job applicants seeking a position at our client’s company. And the scam was perpetrated using publicly-available information – no...








