Phishing emails are as predictable as the sunrise.
If I received a dollar for every fraudulent message forwarded to our team, I’d have more cash than Bill Gates.
Joking aside, I don’t foresee attacks slowing down for the businesses we serve. According to the FBI, there were 241,342 victims of phishing/vishing/smishing/pharming in 2020—more than double the number for 2019 (and the 2018 figure was only 26,379). As Steve put it, “There’s simply no way any IT expert can secure something that’s inherently unsecure—namely email.”
Email can create cybersecurity risk. But this is where education comes in.
In this Tech Tip, we’re going to look at some phishing examples together. When we’re done, I hope you’re better equipped to recognize fraud.
Phishing examples: Actual emails sent to our clients
It’s one thing to discuss an email scam hypothetically, but it’s another thing to see actual phishing examples.
Each of the messages we’ll review was sent to a client. After a picture of the email, we’ll cover what made the email tricky and what gave the email away. Please note that we’ve redacted some details for the sake of those involved.
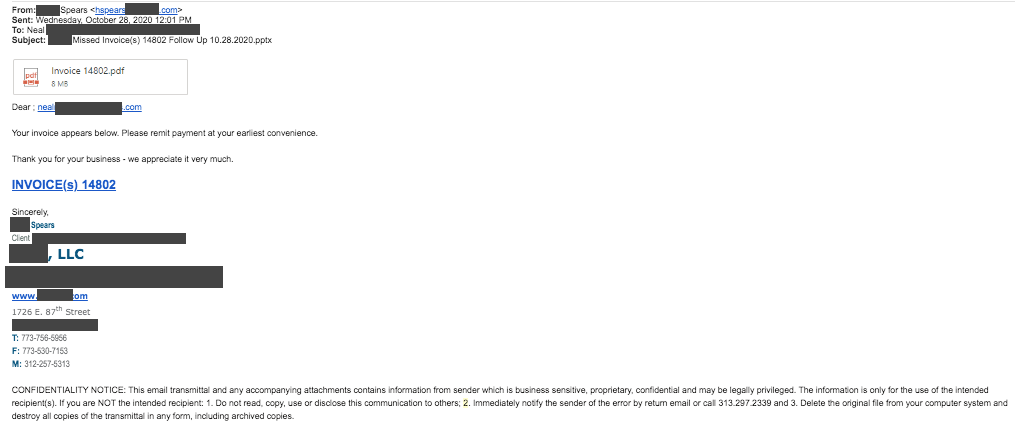
The fake invoice
This is what we call a spear phishing scheme. In this situation, the cybercriminal was trying to trick our client into thinking that his company had an unpaid invoice. After the main message, notice the link. The scammer was hoping that our client would click on this link and provide funds, sensitive credentials, or both.
What made the email tricky:
- This is a real organization that our client had worked with.
- The scammer impersonated a real employee from the organization.
- There’s a legitimate–looking signature.
- There’s a legal–sounding confidentiality notice.
What gave the email away:
- The greeting uses our client’s email address—versus his actual name.
- There’s a subject-verb disagreement in the confidentiality notice.
What happened to our client:
Our client deserves a round of applause for following a cybersecurity best practice and protecting his company from danger. He didn’t click the link. Instead, he picked up the phone and called the organization that had supposedly sent the invoice.
Here’s what he said, “I just found out by calling that this is definitely a phishing email.” Great job!
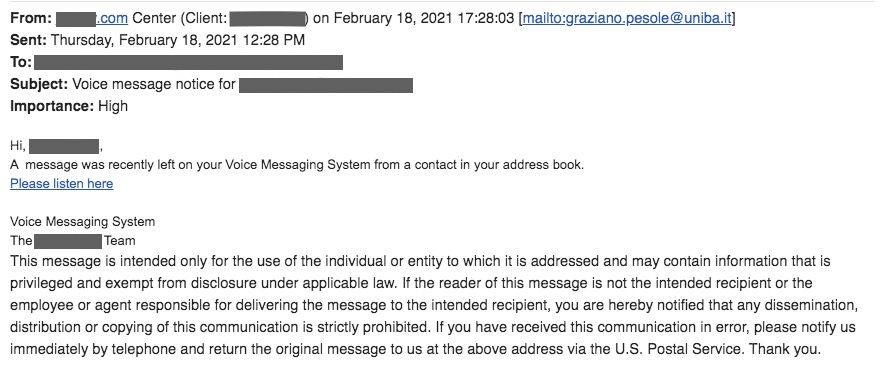
The voicemail scam
To make this larger, please click.
Here’s another phishing ploy you might have encountered: the voicemail scam. In this situation, the bait was a fake message, and the link leads to a phony login site.
What made the email tricky:
- This email almost looks like an automated alert. The main message is to the point, and the cybercriminal doesn’t raise suspicions by asking for money, etc.
- Once again, there’s a legal statement.
What gave the email away:
- The message claims to be from our client’s “Center” versus from our client’s phone system.
- An unusual email address is in the “from” field.
- The greeting contains a comma between “Hi” and our client’s identifier.
What happened to our client:
Our client told us, “I’m assuming this is SPAM since I have no message on my phone…“ Pay special attention to how she determined the validity of the email. I’ll discuss verification toward the end of this Tech Tip.
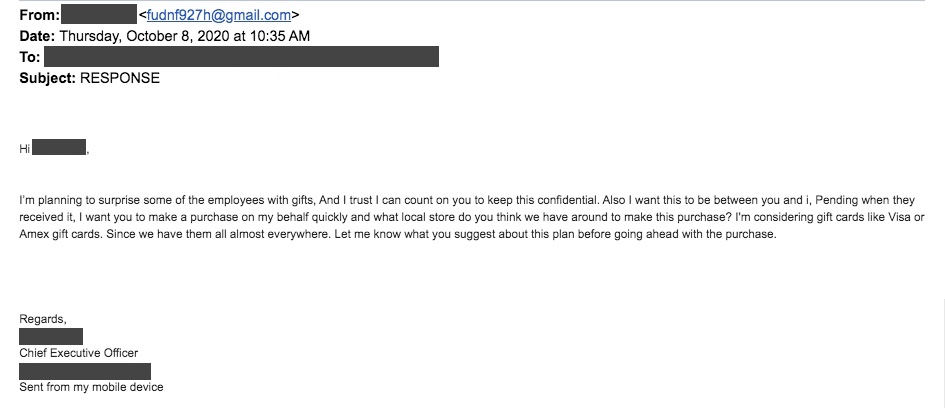
The gift–card scam
To make this larger, please click.
Don’t be surprised if you get a message like this around Christmas! Out of all our phishing examples, the gift–card scam may be the easiest scheme to see through. However, it’s still important to educate yourself about this danger.
What made the email tricky:
- This email impersonates our client’s CEO. Both the “from” field and the sign–off have the CEO’s name.
- The sign–off even contains “Sent from my mobile device.”
What gave the email away:
- The actual email address next to the CEO’s name is clearly not associated with his organization (it’s a Gmail account) and appears to almost be random in nature.
- You don’t need to be an expert in English to see that the writer made errors. “I’m planning to surprise some of the employees with gifts, And I trust I can count on you to keep this confidential.”
- The message causes confusion. “Also I want this to be between you and i, Pending when they received it, I want you to make a purchase on my behalf quickly…” Huh?
What happened to our client:
No gift cards purchased for this cybercriminal!
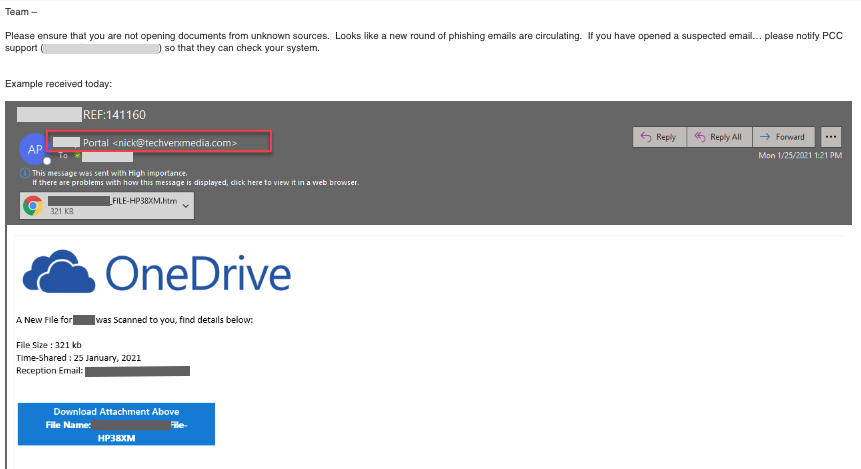
The file scam
To make this larger, please click.
Here’s the final email for our phishing examples. In this situation, the scammer was probably attempting to harvest our client’s credentials through a fake login page.
What made the email tricky:
- This does a good job at imitating Microsoft’s branding. Check out the similarity between the phishing email’s graphic and the graphic in this review.
- The name of the fake file has our client’s name.
- The message gives technical information (e.g., 321 kb).
- There’s a copyright notice below the download button.
What gave the email away:
- As our client rightly pointed out, the sender looked suspicious.
- The message has incorrect capitalization and a comma splice.
- With OneDrive, you would receive an invitation to access a shared folder. However, a legitimate email won’t have an attachment—just a link to OneDrive to accept the invitation.
What happened to our client:
I want to applaud our client for how he handled this incident. In the picture above, you’ll see that he used the email as a teaching opportunity. Way to go!
How to handle a suspicious email
Now that you’ve seen different phishing examples, it might be easier to recognize fraud. But the real test occurs when a suspicious message shows up in your inbox.
When your “vendor” threatens you over an “unpaid invoice,” you might feel uncertain about how to respond. When your “boss” suddenly requests help with a financial transaction, you might feel the pressure to go against your better judgment.
Here are some tips:
- Don’t try to explain away suspicion. There’s a reason you weren’t anticipating an email from your boss while he’s on vacation. Don’t ignore warning bells in your head, but investigate further.
- Verify apart from email. Don’t click a link or download an attachment to see if the communication is legitimate. You should also know that if your email has been hacked, confirming through email isn’t a good choice. Shoot a text to your boss, call the person who sent the invoice, or visit your banking website directly.
- Check the true “from” address. Don’t just rely on the name listed. See if the email address matches the person and company. For example, the name may be your coworker‘s, but when you actually look at the associated email address, it has no relationship to your company whatsoever.
- Examine the greeting. Does the message address you in an unusual way? “Hi JohnDoe@XYZ.com” isn’t a typical opener and might indicate fraud.
- Don’t assume legitimacy because there’s legal or technical information. Even if there’s a confidentiality notice, that doesn’t mean the sender is trustworthy.
- Look for grammar mistakes. Missing punctuation, subject-verb disagreements, or other grammatical issues should raise your suspicions.
In today’s environment, you will face email fraud.
But the more you study different phishing examples, the better prepared you’ll be to avoid security compromises.
If your business wants to train employees on cybersecurity, please get in touch at info@weareproactive.com or 704-464-3075 extension 3.

About Brad Link
Brad serves as our Senior Network Engineer and technical team lead. He designs and implements numerous IT solutions, and our clients benefit from his expertise in networking, cybersecurity, Microsoft products, and more. While you might find him conducting virtual CIO work or product research, he spends a good chunk of his day answering everyone’s questions about everything.



Thanks Brad,
Too many small business owners put all their energy into growing and building their businesses, only to be taken down by not spending a tiny portion of their time working to preserve the business they have built. I have seen small businesses crushed after clicking a single link in an email.
Keep up the good work.